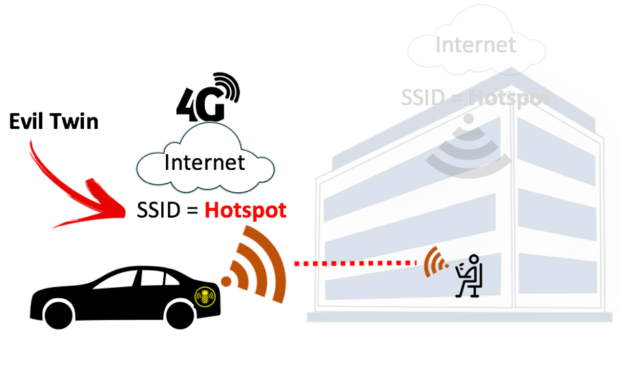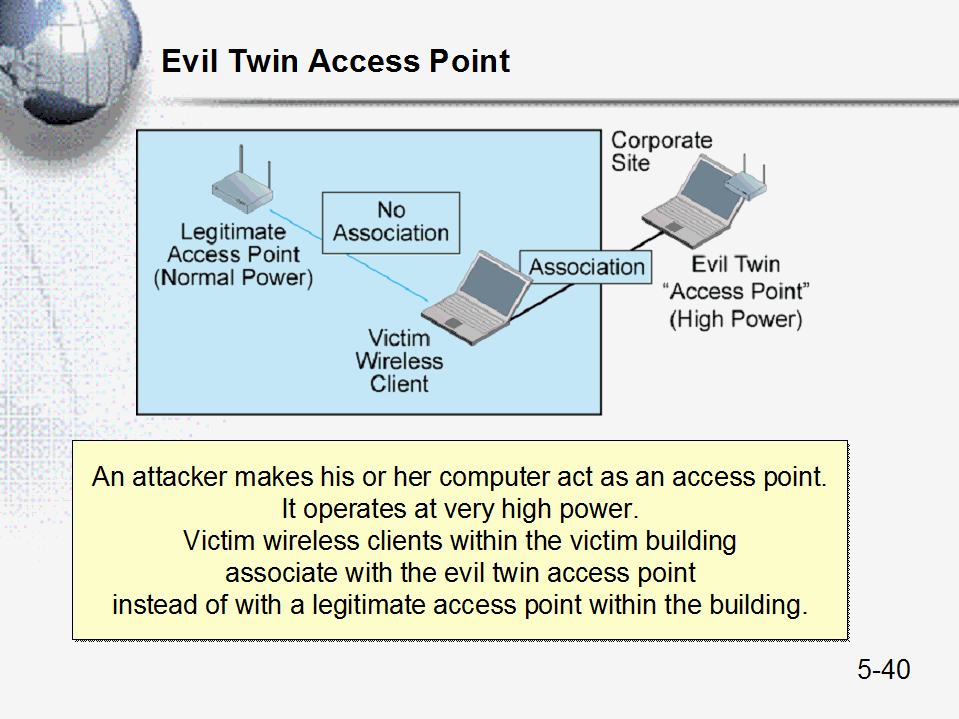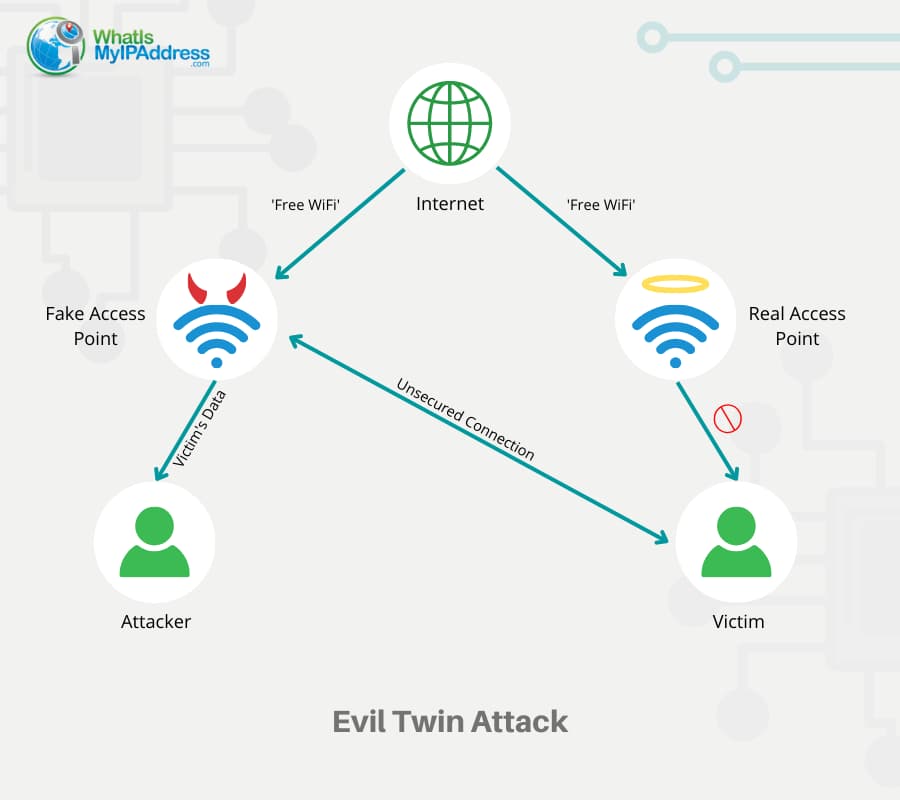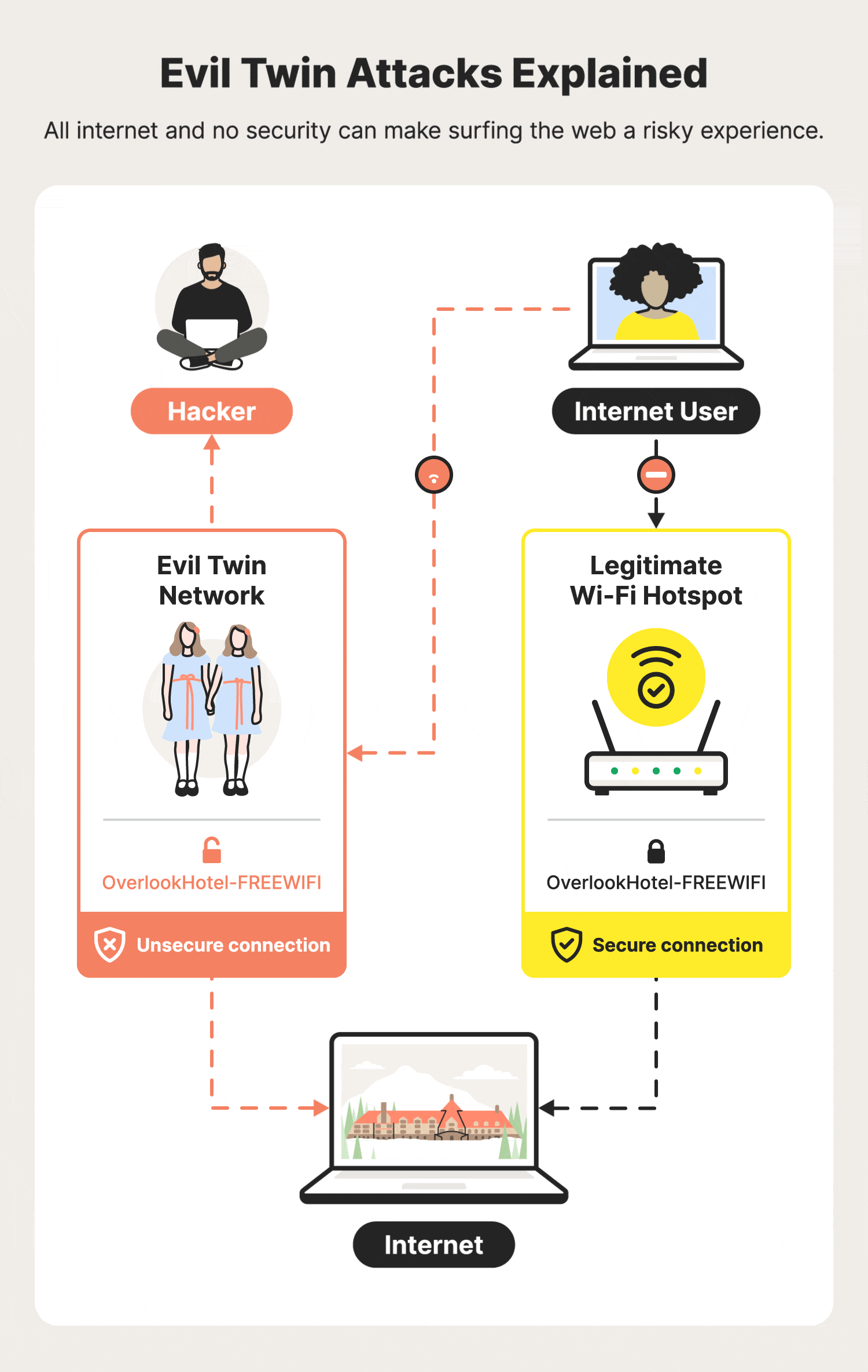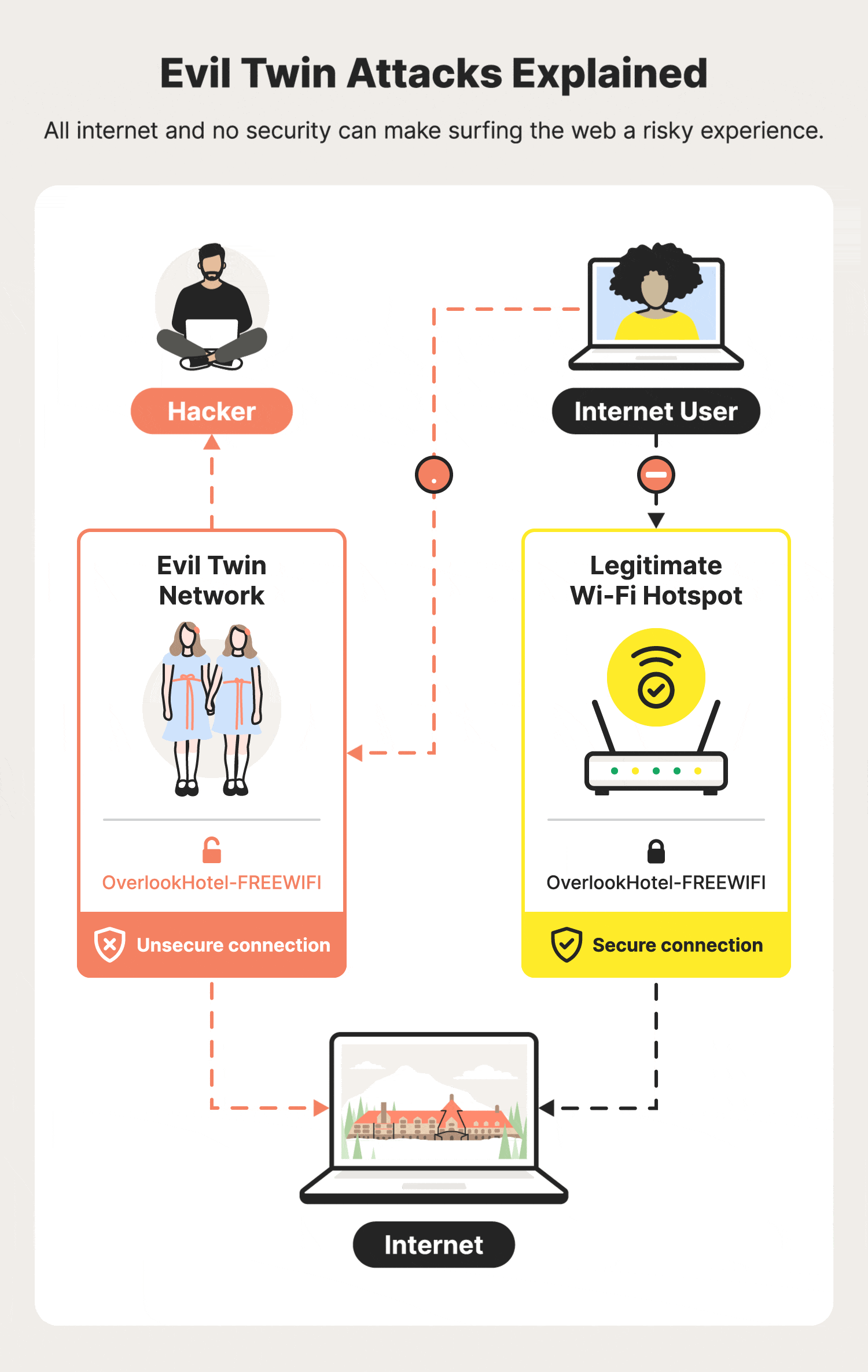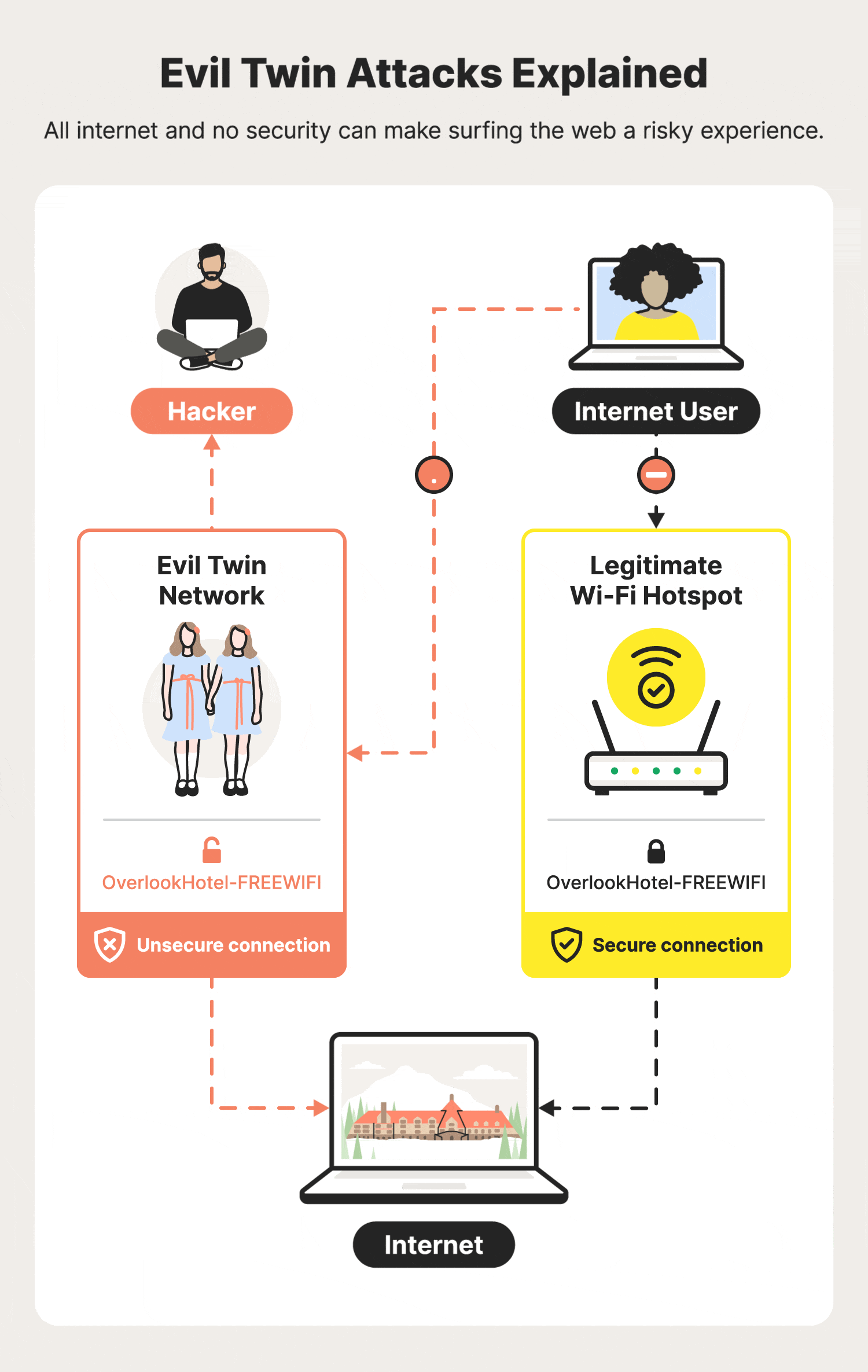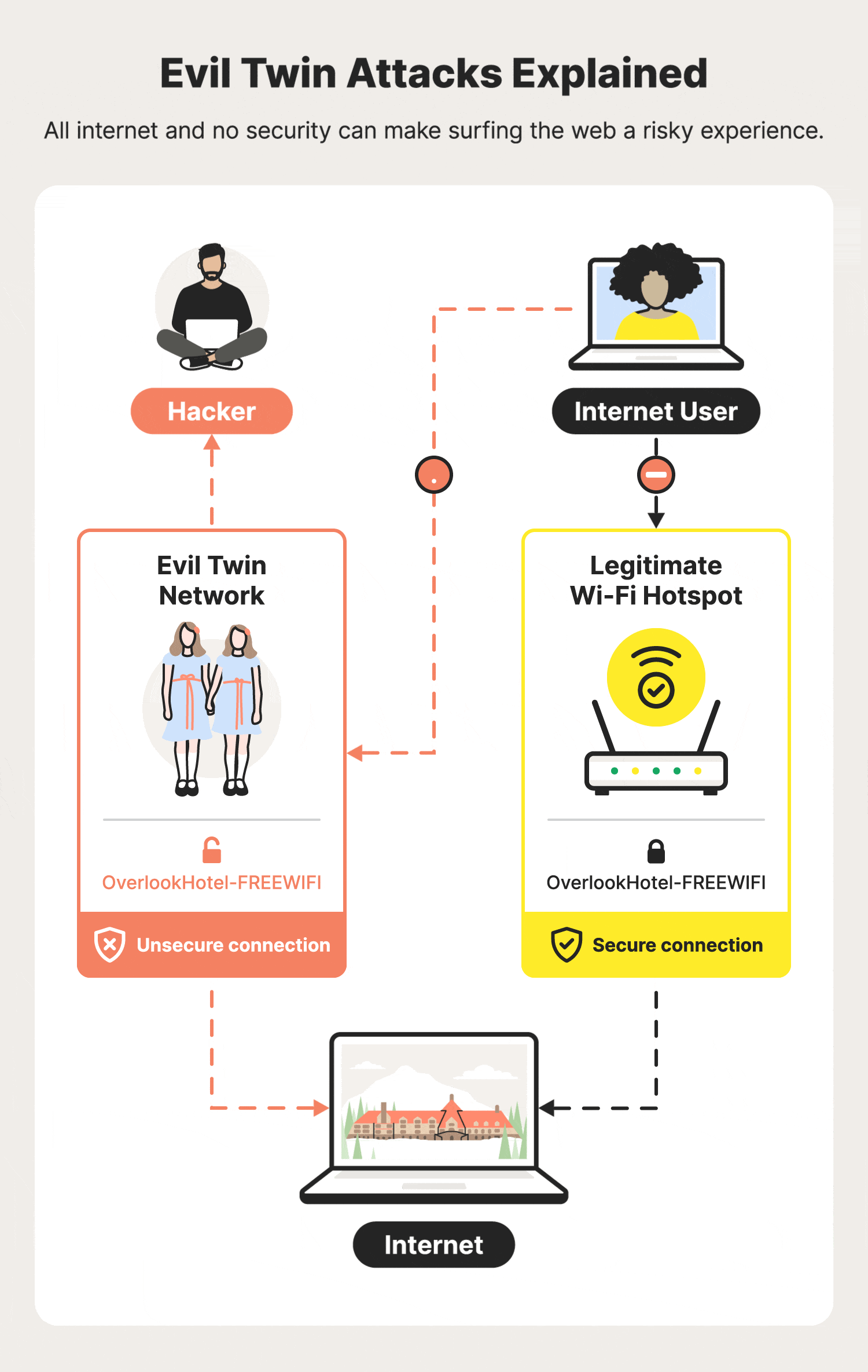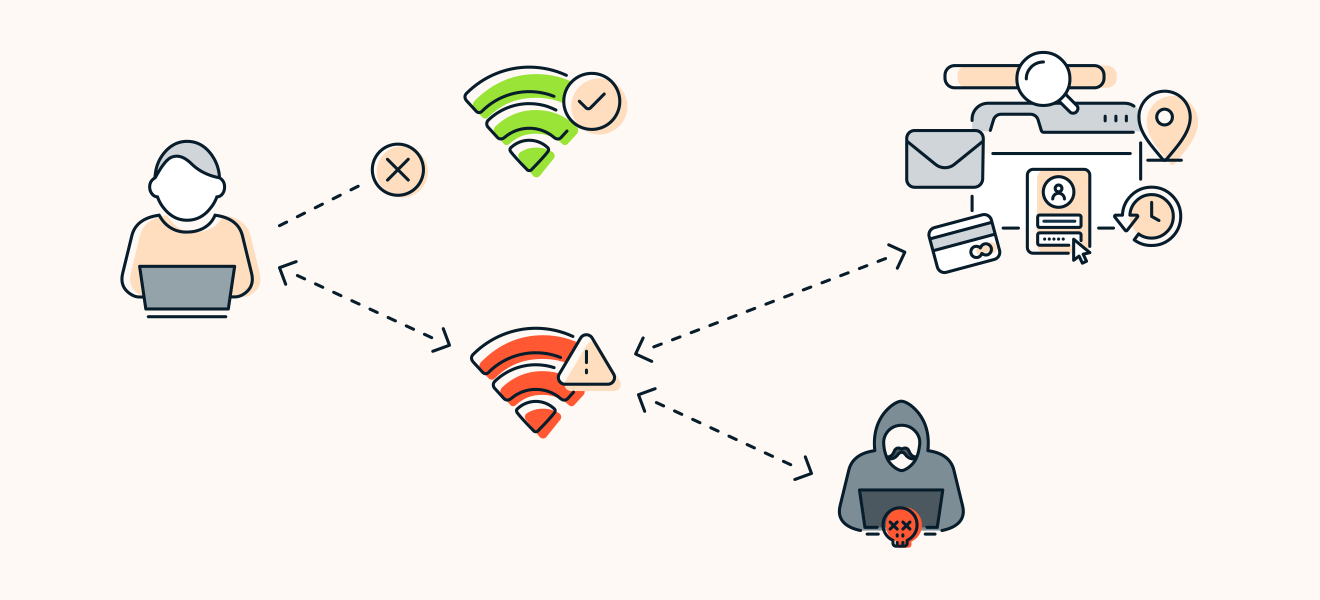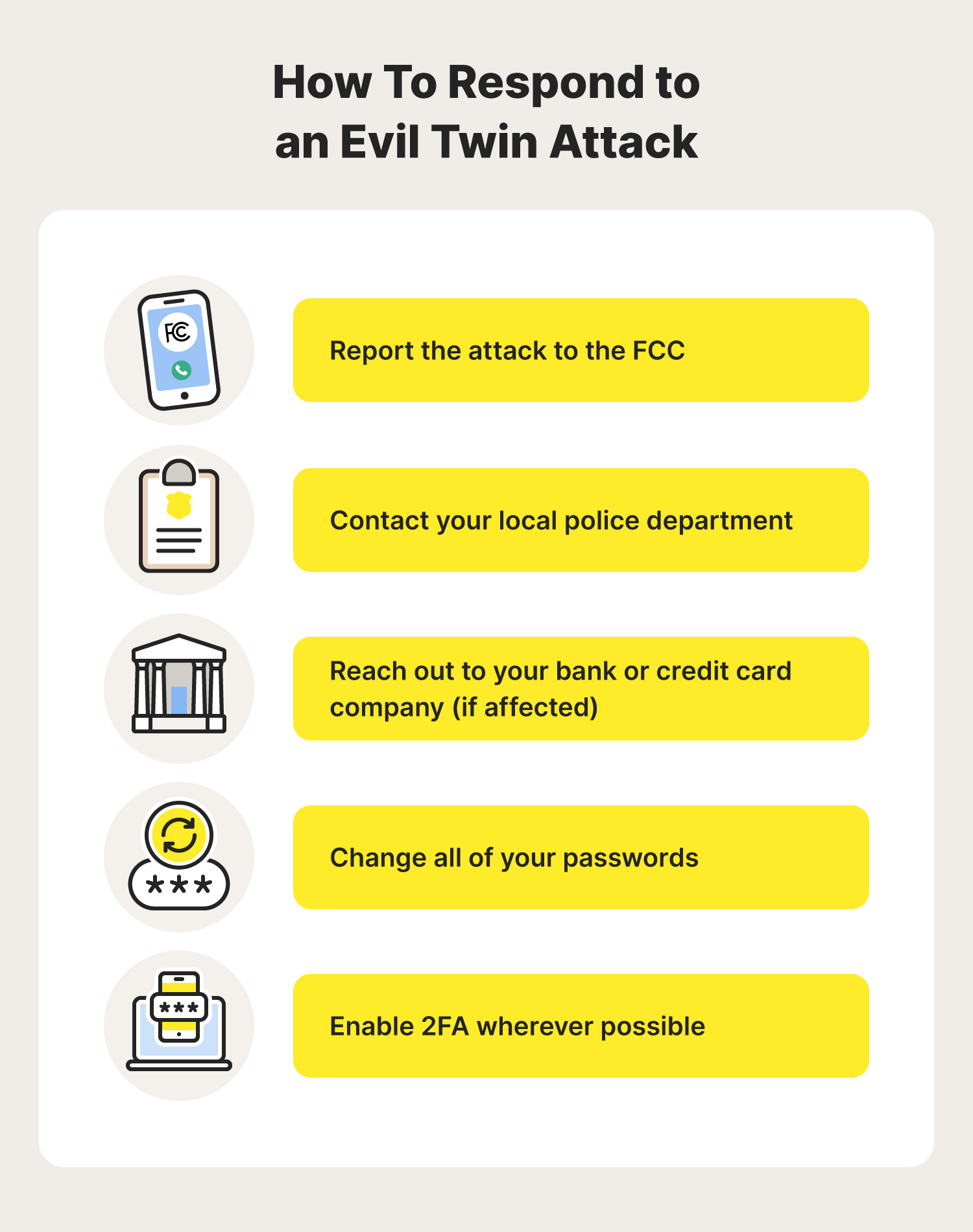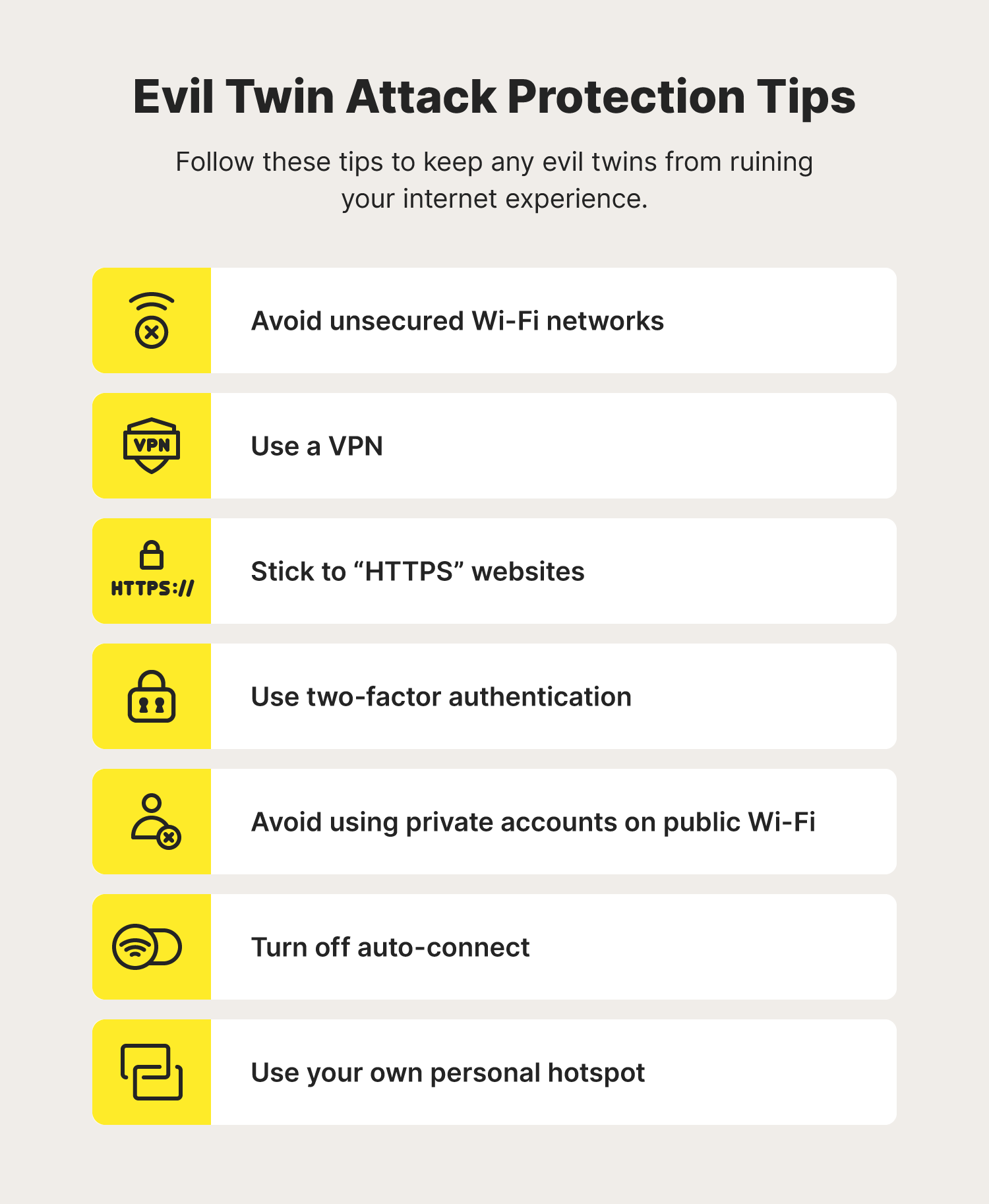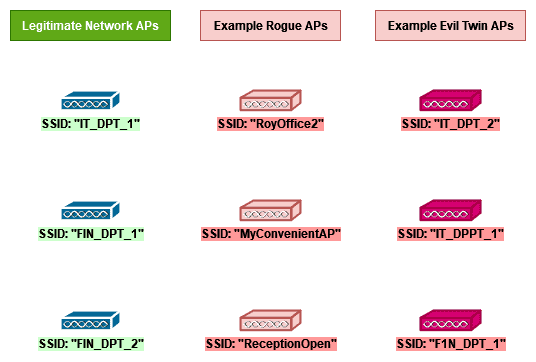
An Efficient Scheme to Detect Evil Twin Rogue Access Point Attack in 802.11 Wi-Fi Networks | International Journal of Wireless Information Networks

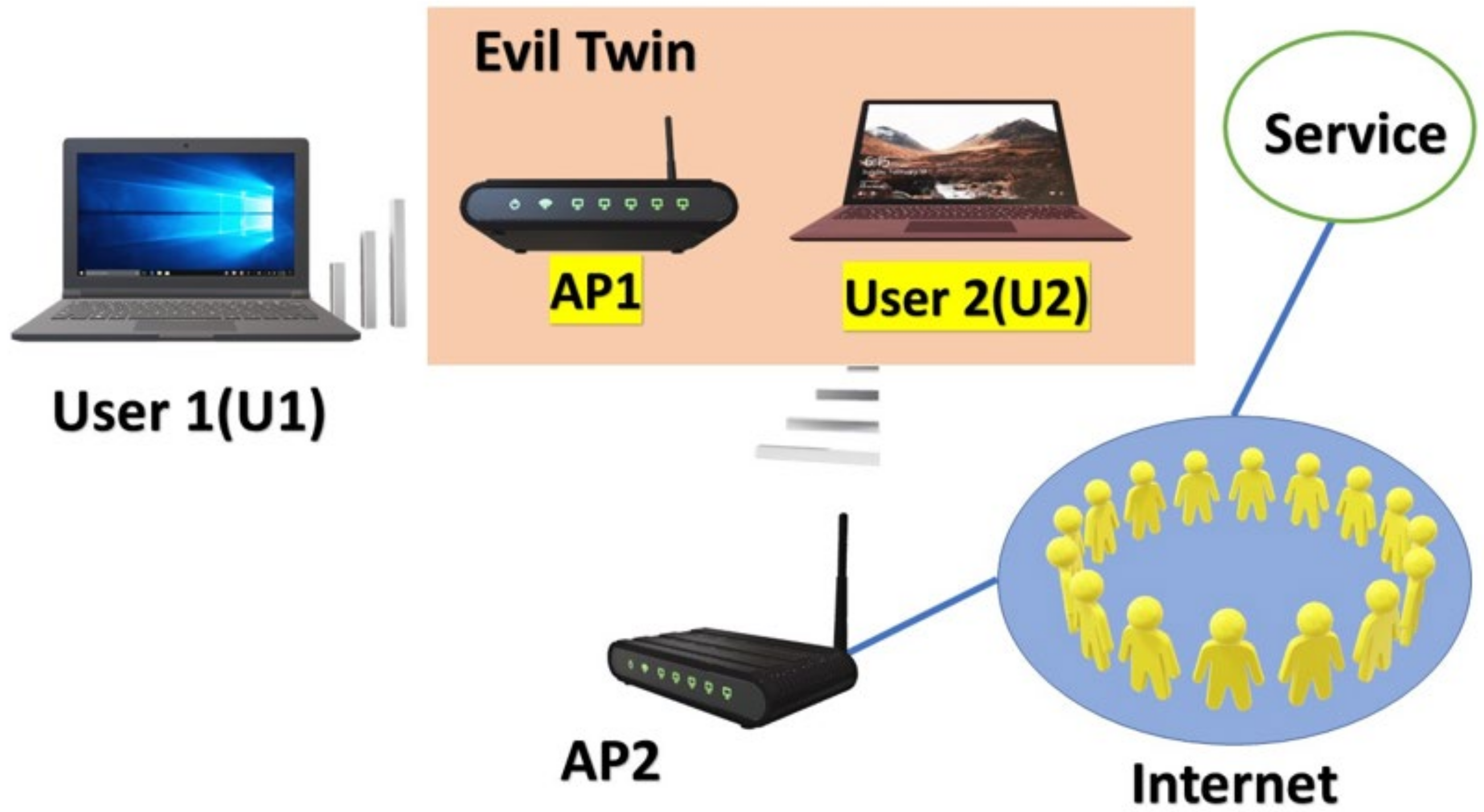
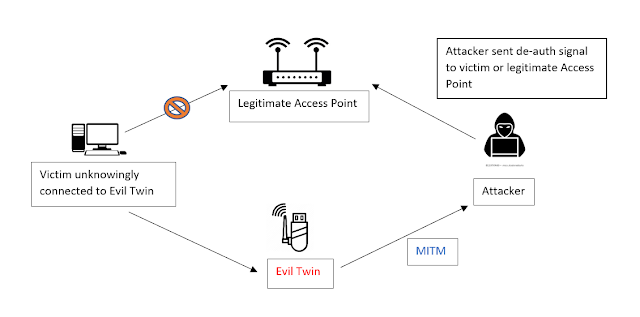
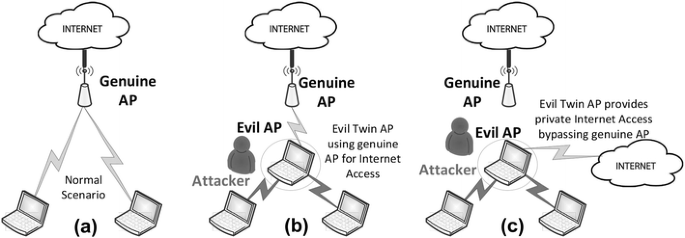
Illustration of an Evil Twin Attack. The attacker can successfully lure... | Download Scientific Diagram